Cryptographic Keys
Agile and future proof encryption management and automation.
Why CZERTAINLY Keys?
Confidentiality of digital communication has become important integral part of secure and reliable solutions. Current trends show that the use of encryption is on the rise within all industries.
CZERTAINLY brings easy and convenient solution to protect our baseline security in every day digital communication by assuring and automating cryptographic keys, certificates, and trust services lifecycle.
CZERTAINLY is designed to protect critical assets and services for customers of any size and type.
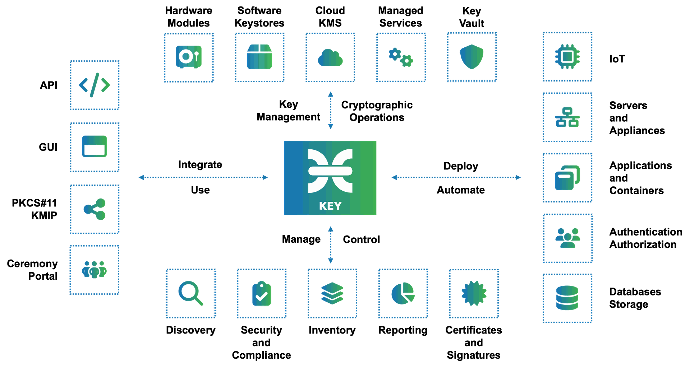
Encryption Management (also known as Cryptographic Key Management) is the set of techniques and procedures that support the establishment and maintenance of keying relationships between the authorized parties.
Key management encompasses techniques and procedures that support:
- initialization of system users within a domain
- generation, distribution, and installation of keying material
- controlling the use of keying material
- update, revocation, and destruction of keying material
- storage, backup/recovery, and archival of keying material
Service-based approach
Fast integration of use-cases
Abstraction of encryption tasks and agility
Easy maintenance of the encryption
Key problems to be solved
Unmature Key Management
Inadequate tools and understanding of encryption management cause issues.
Security and Compliance
Rapid changes in cryptographic algorithms and evolution of post quantum threat. Adoption of standards.
Costs and Resource
Inconsistent manual management of cryptographic keys becomes expensive.
Technology
Future proof, vendor-agnostic approach to management of all keys across the infrastructure.
Agility and Monitoring
Build consistent inventory. Detect and quickly replace non-compliant or deprecated keys.
Automation
Automation of the cryptographic key management operations can save thousands of manhours.
Organizations have one of the top challenge in an encryption strategy discovering where data resides
Organizations have suffered at least one data breach; half experienced a breach within the past 12 months
Organizations transfer sensitive or confidential data to the cloud whether or not it is encrypted
Organizations use hardware security module (HSM) to protect cryptographic keys
Standards need encryption












How we can help
Monitoring compliance of the key management solution including key types, algorithms, usage, expiration, and other cryptographic key attributes and life cycle
Key management policy and procedures design and implementation according specific requirements and standards like PCI, NIST, ISO
Hardware Security Modules (HSM) integration with infrastructure and applications, HSM secure management from the manufacture to decommissioning
Application cryptography life cycle management and testing, cryptographic architecture using software and hardware based keystores
Cloud based cryptographic key migration and encryption management, including BYOK, KMS, cryptographic key management in public and private clouds
Agile and post quantum cryptography implementation, innovative cryptographic protocols, secure multi party computation (SMPC)
CZERTAINLY benefits
Compliance
Reduce the risk of incoherent cryptographic keys and encryption
Centralized
Technology-agnostic, consistent inventory of cryptographic keys
Agility
Instant propagation of all the changes on the profiles
Automation
Automate key generation, replacement, renewal, monitor environment
Cloud-native
Manage cryptographic keys for cloud native applications
Migration
Switch conveniently between technologies and achieve vendor neutrality
Security modules
Protection of sensitive data and keys using security modules and various technologies
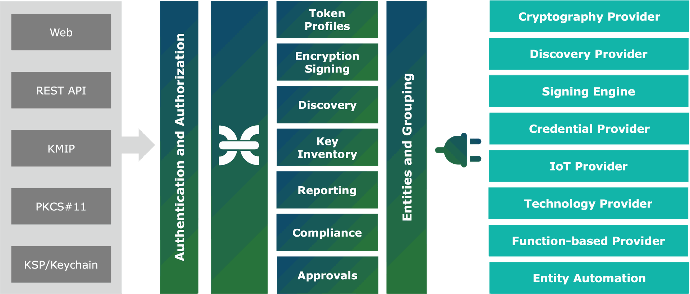
Typical key management process
Build Inventory
Connect technologies as cryptography providers, including software module, hardware module, or clou-based services that maintains keys. Synchronize information about the cryptographic keys and build consistent inventory.
Create Token Profiles
Every application and user has its own requirements for the encryption management. Prepare token profiles that control who and how can use cryptographic keys. Cryptographic protocols can be enabled for any token profile, if needed.
Implement
Implement and automate encryption management. Use with systems where you need to have management of keys and see the overall improvement of the infrastructure on dashboards.
Integrate and Monitor
Integrate with monitoring tools, setup notifications. Monitor infrastructure and update if necessary. Periodically run health checks, synchronization, validation, and maintenance.
Interested in CZERTAINLY?
Your secure and trusted infrastructure!