Digital Signatures
eIDAS compliant solution for digital remote signing, sealing, and timestamping.
Why CZERTAINLY Signatures?
Digital signatures are one of the main tools in electronic communication to protect electronic data, its provenance, non-repudiation, and integrity in any time and high level of confidence.
CZERTAINLY brings easy and convenient solution to protect our baseline security in every day digital communication by assuring and automating cryptographic keys, certificates, and trust services lifecycle.
CZERTAINLY is designed to protect critical assets and services for customers of any size and type.
Owen ready integrations
Fast TSP certification process
Connect your own technology
Configure any use case
Electronic signature assurance

eIDAS (electronic IDentification, Authentication and trust Services) is an EU regulation on electronic identification and trust services for electronic transactions in the European Single Market.
It is legally binding in the EU and also acts as a blueprint for trust services projects all over the world.
Electronic signatures are one of the main tools in the electronic communication. eIDAS recognizes 3 electronic signatures assurance levels:
Qualified (QES)
An advanced electronic signature that is created by a qualified signature creation device (QSCD), and which is based on a qualified certificate for electronic signatures.
Basic (BES)
Data in electronic form which is attached to or logically associated with other data in electronic form, and which is used by the signatory to sign.
Advanced (AES)
Electronic signature which meets the following requirements:
- it is uniquely linked to the signatory;
- it is capable of identifying the signatory;
- it is created using electronic signature creation data that the signatory can, with a high level of confidence, use under his sole control; and
- it is linked to the data signed therewith in such a way that any subsequent change in the data is detectable.
Sole Control Assurance Level 2 (SCAL2)
- The signing keys are used, with a high level of confidence, under the sole control of the signer.
- The authorized signer’s use of its key for signing is enforced by the signature activation module by means of signature activation data provided, by the signer, using a signature activation protocol, in order to enable the use of the corresponding signing key to sign specific documents.
Sole Control Assurance Level 1 (SCAL1)
- The signing keys are used, with a low level of confidence, under the sole control of the signer.
- The authorized signer’s use of its key for signing is enforced by the Server Signing Application Service Component which authenticates the signer. The activation of the signing key can remain for a given period and/or for a given number of signatures.
Compliance
QSCD
EN 419 221-5
Protection Profiles for TSP Cryptographic Modules – Part 5: Cryptographic Module for Trust Services
SAM
EN 419 241-2
Trustworthy Systems Supporting Server Signing – Part 2: Protection profile for QSCD for Server Signing
Sealing
CEN/TS 419 221-6
Conditions for use of EN 419221-5 as a qualified electronic signature or seal creation device
eIDAS formats
ETSI EN 319 142 – PDF Advanced Electronic Signature Profiles (PAdES)
ETSI EN 319 132 – XML Advanced Electronic Signatures (XAdES)
ETSI EN 319 122 – CMS Advanced Electronic Signatures (CAdES)
ETSI TS 119 182-1 (draft) JSON Advanced Electronic Signatures (JAdES)
ETSI EN 319 162 – Associated Signature Containers (ASiC)
ETSI EN 319 422 – Time-stamping protocol and time-stamp token profiles

ENISA guidelines
The European Union Agency for Cybersecurity






CZERTAINLY benefits
Flexibility
Integration with existing front ends, wide support for document management, CRM, and ERP
Efficiency
Support for various use cases including qualified signing, code signing, timestamping
Security
Support for SAM modules and tamper proof QSCD, support by security audits by EU and national authorities
Performance
Unlimited number of processed documents without volume-based fees
Automation
Processing with the highest degree of automation
Compliance
Compliance with GDPR and eIDAS – legally recognized across the EU and beyond
Resilience
Transaction reliability and auditability, non-repudiation, confirmed authenticity, guaranteed integrity
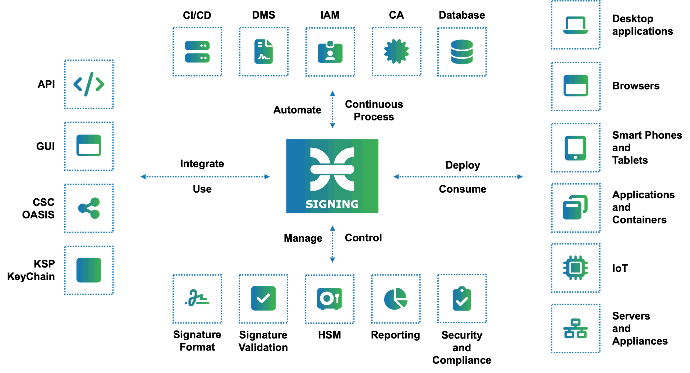
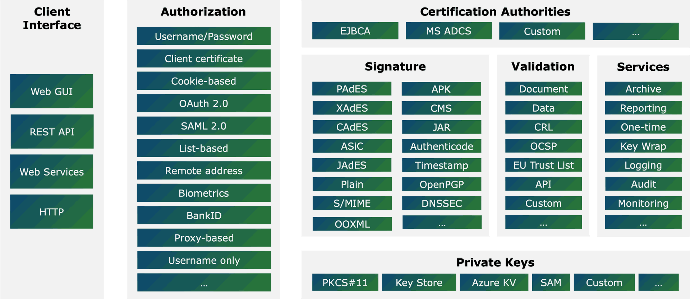
Interested in CZERTAINLY?
Your secure and trusted infrastructure!